Traveling to the Ostrich Saloon in the Scaredy Kite Heights section of the Island of Misfit Toys we can find Rose Mold and the Linux PrivEsc challenge
Talking to Rose we can see they are a Troll from Holiday Hack 2021. They challenge us to complete the PrivEsc challenge and say they’ll tell us why after we complete it.
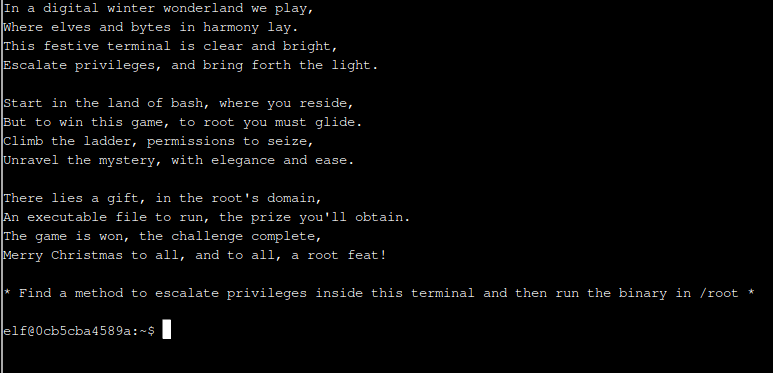
Opening the challenge we get the above poem and task. Find a way to become root and run the binary. We also get two hints in our badge. The first is
Use the privileged binary to overwriting a file to escalate privileges could be a solution, but there’s an easier method if you pass it a crafty argument.
The other hint points us this link with several techniques we can use. This link is what we will start with. Exploit 1 from the list isn’t going to work as the kernel has already been updated. We can verify this with uname -a. Exploit 2 is no good either as netstat isn’t even installed and ps -aux doesn’t return anything of use. With exploit 3 we start to get somewhere.
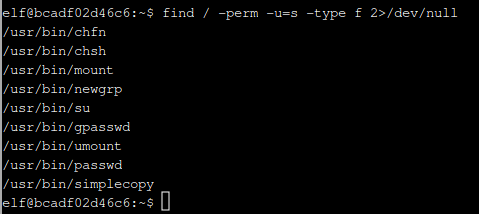
Running find / -perm -u=s -type f 2>/dev/null gives us the above list of programs. Most aren’t anything of note but simplecopy is a program I don’t recognize. Searching google for the man page doesn’t reveal anything which means we’re probably on the right track. Running the program reveals that it takes 2 arguments <source> and <destination>.
The Hard Way
Now this is the point in my initial solving of the challenge that I fell down the rabbit hole. I started with trying to copy the binary out of the root directory with simplecopy /root/* ./runtoanswer and this did successfully copy the file but the permissions were still locked in terms of running it. “No worries” I thought. I can just run simplecopy /root/* /dev/stdout >> ./runtoanswer. Once again this did get me the executable and I could even run it this time but now I had a new error.
Something went wrong reading the configuration file /etc/runtoanswer.yaml: Couldn’t open file: Permission denied (os error 13)
If this persists, please ask for help!
That YAML file is hardcoded into the binary. I tried making or replacing copies of it with no effect. What I was able to do is review the contents of the YAML file to get the answer for the program of santa. At this point I went back to the drawing board and kept reading the hint that got me here. The next technique talked about using a corrupt cron job to run a c program as root that would pop a shell. I didn’t have a cron job to use easily like the task but I figured I could create the same c program and compile it, then use simplecopy to replace one of the other SUID binaries with my rootme program. I wrote my program with an echo command, compiled it with gcc and replaced the mount command with my new program. afterwords running mount dropped me in a root shell and I was able to run ./runtoanswer santa and complete the challenge.
The Easy Way
Despite already having this challenge completed the other hint I had gotten about an easier way to do it kept nagging at me. This was further amplified by people in the very helpful Discord server talking about this other, simpler solution. It wasn’t until I saw chris_jd mention a hint about wrapping the arguments in quotes that the solution hit me in the face. I logged back into the challenge and simplecopy HELP "newfile;/bin/bash"
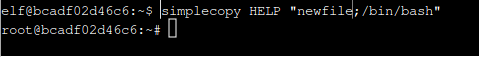
Bam. Root shell in two commands. I ran the program again for good measure and it worked perfectly.
Regardless of how the challenge was completed once we are done we can talk to Rose again. Unfortunately instead of providing info as to why they wanted us to complete the challenge the only response we get is “Nunya!” They do ultimately reveal that there’s a hidden uncharted area around the coast of The Island of Misfit Toys however and there may be similar spots on the other islands.
Leave a Reply