
Continuing West from the Snowball Fight task we will come across Santa’s surf Shack. Inside we can find Ginger Breddie and the Linux 101 task.
Talking to Ginger he doesn’t have any hints to provide us but asks if we would care to join him in a Linux session. Opening the terminal we are greeted with the below prompt.
Looks like we will have several tasks to complete around getting comfortable with the Linux OS. we’ll kick it off by entering yes in the prompt.
The first task is to list the files in the home directory. ls solves this easily. This reveals the first Troll. A file named troll_19315479765589239. Our next task is to find the Troll inside the Troll. We can do this by running cat troll_19315479765589239. That prompts us to remove the Troll which we can do with rm troll_19315479765589239.
With the first batch of trolls eliminated we are next directed to find the present working directory. This is done by running pwd. After running this it appears that there’s still a hidden troll in our directory. We can reveal him by running ls -la to reveal .troll_5074624024543078.
Our next task is to find the troll in our command history. This is done by running history. Then we need to find the troll hiding in our environment variables. We can view this with env
The next batch of challeneges take place in the Workshop directory. We can run cd workshop to begin them. One of the Trolls is hiding in one of the many files in the workshop. We can reveal him with grep -i 'troll' * to find him in toolbox_191.txt
Next we need to run the present_engine binary this binary is not currently executable. This can be fixed by running chmod +x present_engine then ./present_engine
Next we need to proceed into electrical to fix some broken fuses. blown_fuse0 can be renamed to fuse0 with the command mv blown_fuse0 fuse0. Next we want to increase the fuse redundancy by symlinking a new fuse named fuse 1 to fuse0. This can be done with ln -s fuse0 fuse1. We further increase the redundancy of the fuses by making a copy of fuse1 named fuse2 with cp fuse1 fuse2. Then as a final measure here we add in some Troll Repellent to Fuse 2 with echo "TROLL_REPELLENT" > fuse2.
Now we need to switch directories to /opt/troll_den and find a troll inside there. We can use the find command to do this with the command find . -iname troll*. Next we need to find the file owned by the troll user. We again use find with find . -user troll. Then we need to find the file in between 108 and 110 kilobytes. We can do this with find . -size +108k -size -110k.
We’re almost at the end now. Our next task is to list the running processes. This is done with ps -aux. Then we need to look at listening TCP ports. We can see this with netstat -lnp. Our last troll can be retrieved by interacting with the HTTP server at port 54321. We can do this with curl 127.0.0.1:54321
The last thing we need to do is stop the 14516_troll process. We first need to identify the PID of this process with ps -aux.
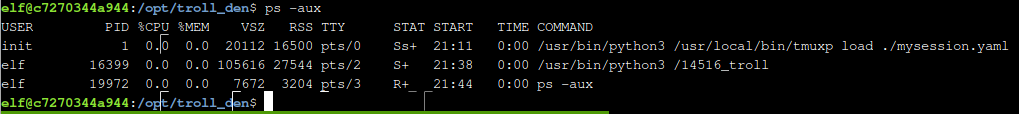
Looking at this output we can see the PID is 16399. Running kill 16399 completes the task.
Talking to Ginger Breddie after this challenge still doesn’t give any information but the challenge has been completed and we can move onto the next one.
Leave a Reply